Article written by J Bryant Vásquez
The day we’ve been talking for well over a year is finally upon us. With the 32 CFR final rule becoming effective on December 16, 2024, the Cybersecurity Maturity Model Certification (CMMC) program is entering a new phase of implementation for the Defense Industrial Base (DIB). This marks a pivotal shift toward enhancing the security and resilience of the nation’s defense supply chain.
As a refresher, CMMC is a critical initiative designed to safeguard Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). For those operating in the DIB, this program brings substantial changes to how business is conducted. Whether you’re well-prepared or still catching up, this guide will help you understand what you need to know—and the steps you should take—to ensure compliance and maintain your competitive edge.
What is CMMC?
CMMC is designed to protect FCI and CUI from evolving cybersecurity threats, enforcing a unified standard across the DIB. Following public feedback, the DoD revised the program, simplifying compliance, and aligning it with the National Institute of Standards and Technology (NIST) standards like SP 800-171 and SP 800-172.
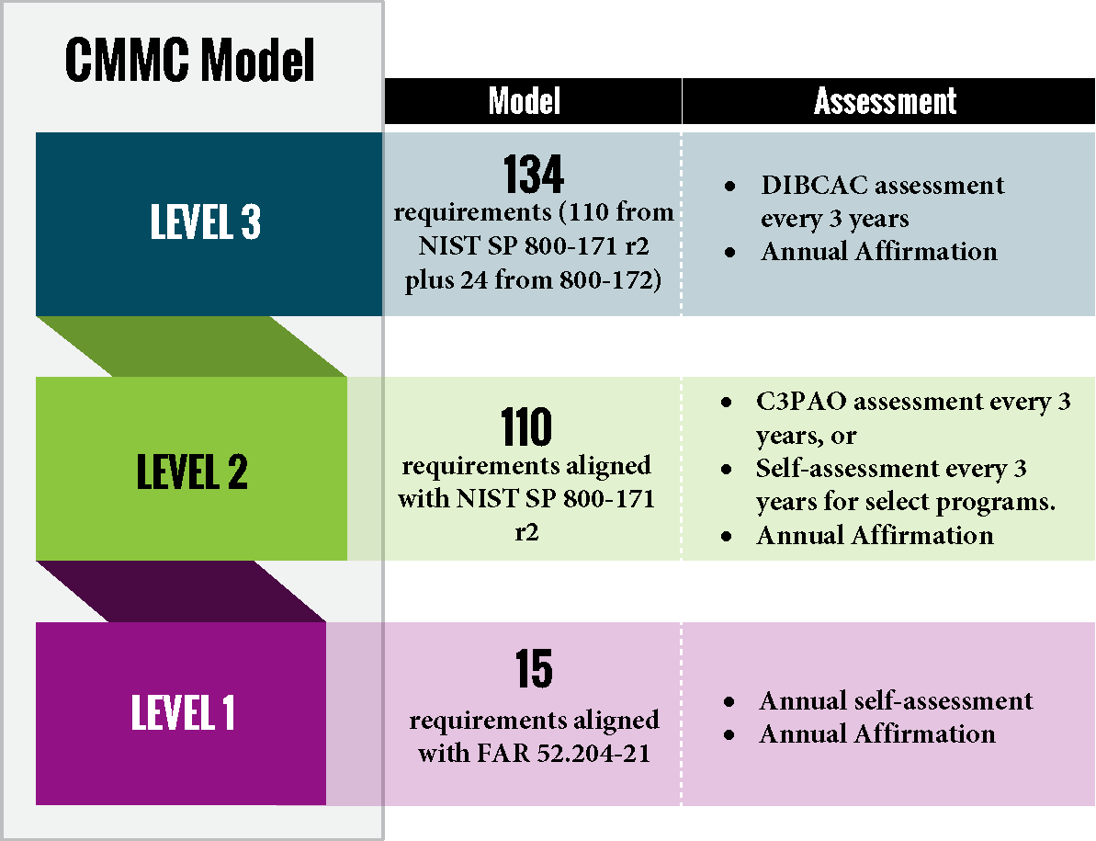
The model has a three-level structure:
- Level 1: Basic safeguarding for FCI.
- Level 2: Comprehensive protection for CUI (based on all 110 NIST SP 800-171 controls).
- Level 3: Advanced safeguards against persistent threats (includes selected NIST SP 800-172 controls.
Key Deadlines and Phased Rollout
- December 16, 2024: 32 CFR rule becomes effective, authorizing official assessments and making them commercially available.
- Early 2025: Around March, the 48 CFR acquisition rule is expected to be finalized, embedding CMMC requirements in contracts.
- Phase 1 will commence with certain solicitations requiring contractors to complete Level 1 or Level 2 self-assessments, as applicable.
- 2025–2028: The program will roll out in four phases, gradually enforcing compliance and certification across all DoD solicitations.
- Phase 2 (12 Months After Phase 1): Applicable solicitations will begin requiring Level 2 Certification.
- Phase 3 (24 Months After Phase 1): Certain solicitations will mandate Level 3 Certification as applicable.
- Phase 4 (36 Months After Phase 1): Full implementation where all solicitations and contracts will require the appropriate CMMC level for the contract award.
This reflects the gradual enforcement of compliance and certification across all DoD solicitations from 2025 to 2028.
The four-phase rollout provides time to train assessors and allow organizations to align their systems with CMMC requirements.
Immediate Actions for Contractors
- Assess Your Organization: Identify whether your contracts handle FCI, CUI, or both, and determine your required CMMC level.
- Self-Assessment: Evaluate your current cybersecurity practices against NIST SP 800-171 controls and NIST SP 800-171 A objectives. Identify gaps and develop a remediation plan to a passing score.
- In Phase One of the CMMC rollout and for the assessment, achieving a score of at least 88 is crucial for organizations aiming to remain part of the Defense Industrial Base (DIB). This benchmark represents the minimum passing score for Level 2 assessments under the CMMC Scoring Methodology. Falling below this threshold could jeopardize your eligibility for DoD contracts and certification, impacting your organization’s ability to contribute to critical national defense projects.
- Assessments:
- Level 1: Perform annual self-assessments.
- Level 2: Undergo evaluations by a Certified Third-Party Assessment Organization (C3PAO) every three years, while conducting annual self-assessments with annual affirmation from senior level officials in SPRS.
- Level 3: Government-led assessments for sensitive operations.
- Partner with Experts: Work with your internal or external team of specialists to prepare for assessments and address compliance gaps effectively.
Plans of Action & Milestones (POA&M)
CMMC 2.13 introduces limited use of POA&Ms:
- POA&Ms are not allowed for CMMC Level 1.
- Self-Assessment POA&M closeout are conducted by the Organization Seeking Assessment (OSA).+
- POA&Ms must be closed out within 180 days of when the CMMC Assessment results are finalized and submitted to SPRS or CMMC eMASS.
Failure to meet these timelines may lead to certification revocation and loss of contract eligibility.
Global Impacts and Opportunities
CMMC compliance is poised to extend beyond the DoD, with other agencies like NASA and DHS considering adoption. International partnerships are also forming, with Canada establishing reciprocity through the Canadian Program for Cyber Security Certification (CPCSC). Similar agreements with countries like Germany, Japan, and South Korea are under discussion.
The Cost of Waiting
Failure to achieve compliance could mean exclusion from future contracts. Preparation is essential, as most organizations require 6–18 months to implement necessary changes and pass certification.
Key Resources to Begin Now:
- 47G Impact Center: The 47G Impact Center, a strategic partnership between 47G and iMpact Utah, is your go-to resource for CMMC compliance certification. With a deep understanding of the evolving CMMC standards, the 47G Impact Center provides expert guidance and support to help organizations achieve and maintain compliance. Led by Bryant Vasquez, a dedicated Utah MEP resource closely aligned with NIST, the center ensures that businesses receive up-to-date information and best practices to navigate the complexities of CMMC requirements. Email Bryant@impactutah.org to start meeting compliance standards and secure DoD contracts.
- Find a Specialist: Visit your local MEP, NIST, MEP National Network
- Utah MEP: Utah-MEP is the premier provider of manufacturing improvement services in Utah. We provide hands-on training & solutions that help manufacturers grow & thrive.
- Summit V: Our partners at Summit V provide full-scope assessments for companies looking to become CMMC compliant. Their team of cybersecurity experts has decades of experience working with NIST cybersecurity frameworks, and have been preparing for years to help organizations implement CMMC requirements.
Now is the Time to Act
With cyber-attacks on the DIB surging in the last years, ensuring compliance is not just about securing contracts, it’s about protecting national security. Organizations that start now will gain a competitive edge, ensuring business readiness when they need to go under the CMMC assessment.
Stay proactive. Secure your future.




